Enumerating in ethical hacking is the process of getting shared resources, users and passwords of the target. Of course, there are several tools that Kali offers us to do this. Here are a few that I’m going to demonstrate.
1. wpscan
Wpscan is a wordpress vulnerability scanner. There are several uses of wpscan, including enumerating users and passwords. So let’s enumerate jo1.pentest.id and look for users.
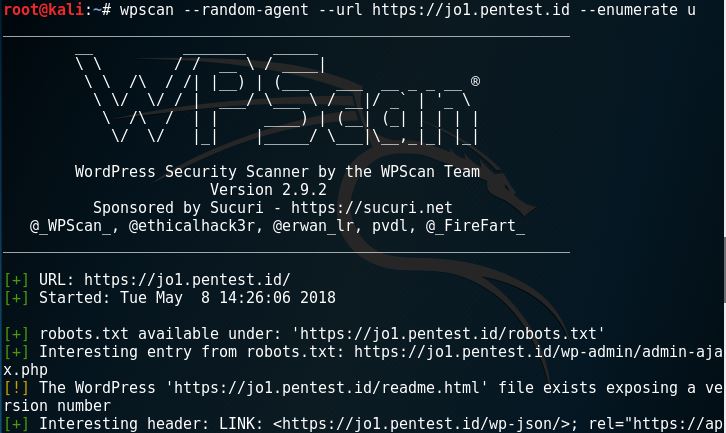
The process might take awhile, but the long wait might also bear fruit. So here is what we get from enumerating users with wpscan.
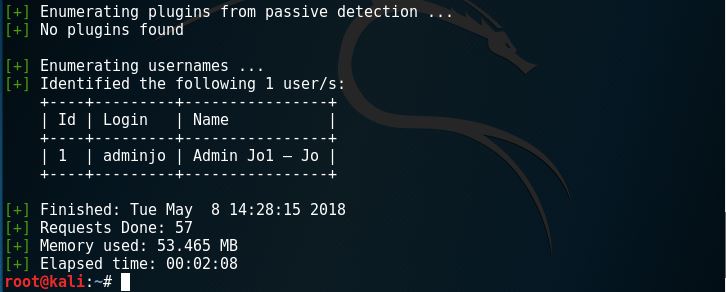
Now that we know the username, we would like to know the password. In this case, we’ll try dictionary brute forcing with wpscan. First, we’ll have to create the ‘dictionary’. The dictionary is the list of word trials that we want wpscan to use to try breaking in. Let’s create a file called ‘pass’. Type in “nano pass” and we’ll get into the text editor.
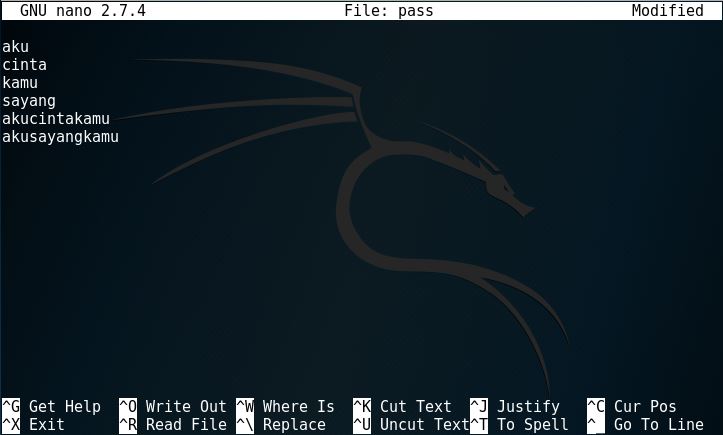
Exit and save the file. Now we go to wpscan again and do this.
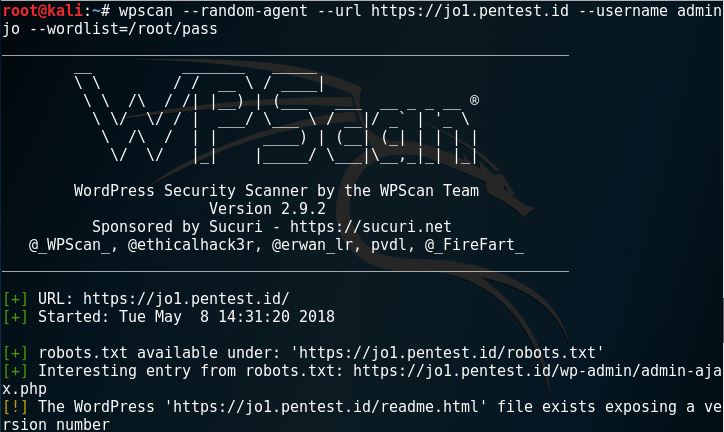
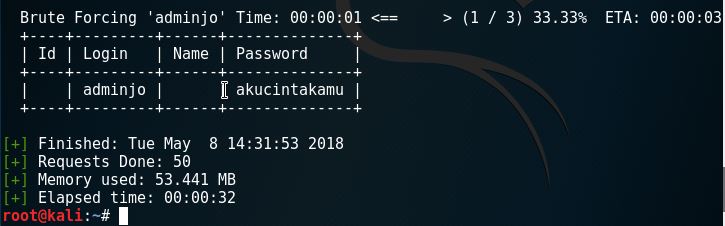
What the command does is try to use adminjo as the user and use the dictionary of passwords that we created to try and get through. It will also take awhile, or also, we might even fail to get it. There are other ways to check if we fail to get the password, but we’ll focus on this one first.
Here is the result of wpscan’s dictionary brute forcing.
2. theharvester
The objective of theharvester is to gather emails, subdomains, hosts, employee names, open ports and banners from different public sources like search engines, PGP key servers and SHODAN computer database. Let’s try using it.
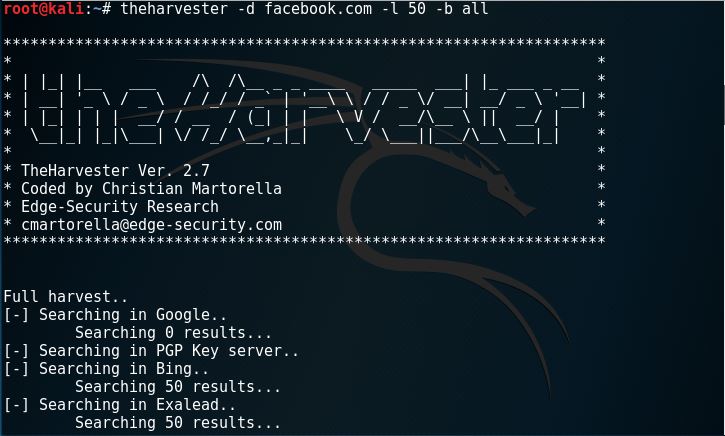
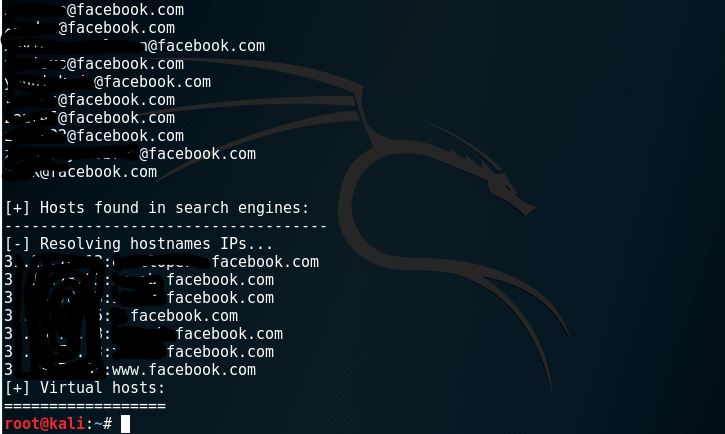
From the command, -d facebook.com means that the domain we want to search on emails is facebook.com. -l 50 means that limit the search to 50 and -b all means that we search by all the search engine such as google and bing. Here are several results of the search, including several hosts.
3. Metasploit
Metasploit provides a public resource for searching vulnerabilities and gives the opportunity for the users to create and develop codes for exploiting. Let’s try and use it.
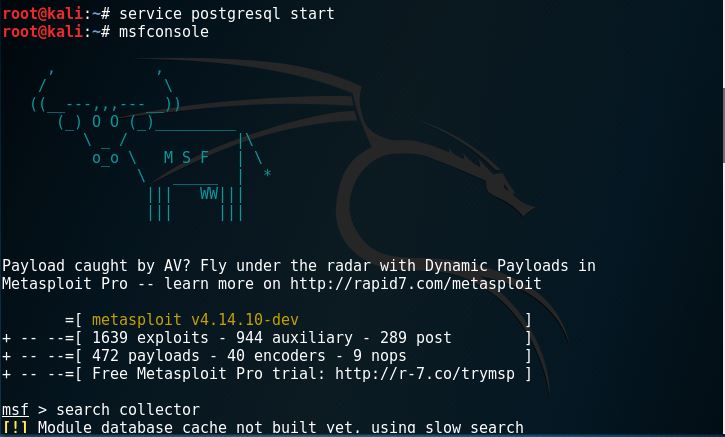
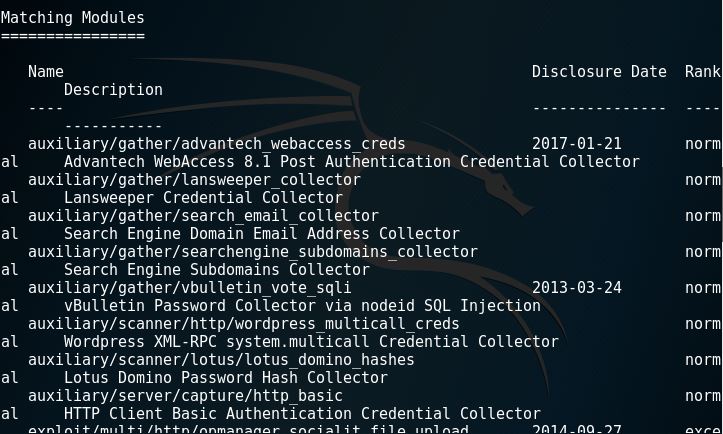
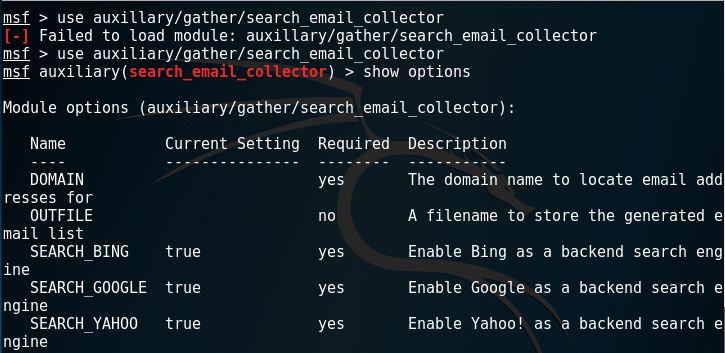
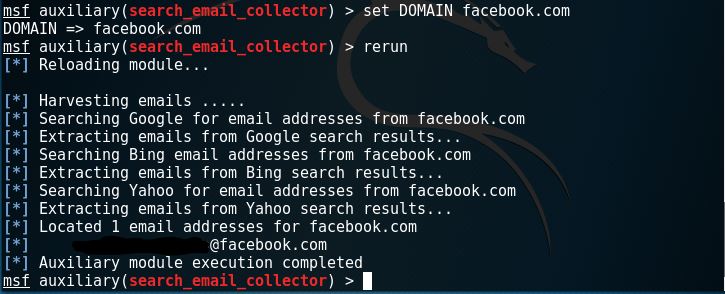
As shown above, using metasploit, we have successfully retrieved 1 email address.
References
https://wpscan.org/
https://tools.kali.org/information-gathering/theharvester
https://whatis.techtarget.com/definition/Metasploit-Project-Metasploit-Framework